The United States has started using this method to steal trade secrets from Chinese companies
A few days ago, the National Internet Emergency Center announced two cyber attacks by the United States against large scientific and technological enterprises and institutions in China
According to Tan Zhu's statistics on the recent two years of cyber attacks in the United States, the main body of US attacks is changing. In addition to well-known entities such as the Central Intelligence Agency (CIA), the US military is increasingly launching cyber attacks against foreign countries
Why did such a change occur
Tan Zhu has previously sorted out the intelligence agencies in the United States, which can be divided into:
individual intelligence agencies such as the Central Intelligence Agency (CIA)
intelligence agencies of the US Department of Justice, including the Federal Bureau of Investigation (FBI) and the National Security Intelligence Agency (ONI)
intelligence agencies under the respective business departments of the US Treasury, Department of Energy, State Department, etc.
the US Cyber Command (USCYBERCOM) of the military system
Now, a large number of cyber attacks against foreign countries are carried out by the US Cyber Command.. The US Cyber Command is under the jurisdiction of the US Department of Defense and is an intelligence agency of the US military
That is to say, the US military has become the main body of cyber attacks
This can also be confirmed in the policies of the United States. In the newly released National Cybersecurity Strategy Implementation Plan of the United States this year, the number of times the term "US Department of Defense" appears has increased by about 30% compared to last year
The newly added section mentions the implementation of the US Department of Defense Cybersecurity Strategy, which is the first strategy developed by the US Department of Defense based on major cyberspace operations
Looking at this strategy, Tan Zhu found that its operational implications were very clear, explicitly mentioning the need to "win national wars in cyberspace and establish asymmetric advantages over other countries"
Previously, the US Cyber Command had conducted 37 "forward hunting" operations in 20 countries around the world, conducting militarized cyber attacks and operations by dispatching cyber warfare forces overseas. Now, such actions are still intensifying
To better understand the US military's emphasis on cyber attack capability, we can start with these two cases announced by the National Internet Emergency Center
These two cases involve a certain advanced material design and research unit and a large high-tech enterprise in smart energy and digital information in China, respectively, and the stolen information is commercial secrets
In cyber attacks, stealing trade secret information is mainly aimed at gaining a competitive advantage in economic competition. Trade secret information includes the assets, personnel, internal organizational structure, development direction, and other information of the enterprise. But the purpose of stealing this information is not limited to this, and the United States can further launch other destructive actions based on this
Last year, a study funded by the US State Department found that China has a leading advantage in all 12 categories of advanced materials, and 7 categories are significantly ahead, including nanoscale materials, coating materials, advanced composite materials, etc
It is worth noting that this study has also become a reference information for the US China Economic and Security Review Commission, an official organization specialized in evaluating China's economic development
These materials are mainly used in industries such as semiconductors, aerospace, and medical devices. These industries are precisely the key sectors in which the United States plans to engage in strategic competition with China
In the face of these issues, the solution proposed by the US economic and trade authorities is to contain China's development through "decoupling and chain breaking". But the thinking of the US military is more direct
The United States Military Academy at West Point has an institution dedicated to providing intellectual support to the US military - the Institute of Modern Warfare. This year, the agency conducted research on the US military's views on national security and found that US military strategists, planners, and combatants are frustrated with China's rise and tend to take action
Therefore, the US military holding this mindset will have more dangerous strategic goals, including "significantly weakening the Chinese economy" and "seeking complete decoupling of the two economies"
In addition, the US military targets Chinese companies not only for economic purposes
The other event announced this time involves the fields of energy and digital information, which belong to the critical information infrastructure sector. Currently, most of the critical information infrastructure in countries around the world is operated by enterprises, but they affect national security. This incident reflects that national security remains the focus of US cyber attacks on us, and this has not changed for a long time
Data shows that in the first quarter of this year alone, there were over 2000 cyber attacks from the United States mainland and its overseas military bases worldwide, targeting multiple countries including China, mainly critical information infrastructure and other targets
The high frequency is due to the low threshold for launching network attacks
The two incidents announced this time have one thing in common, that is, the attackers used vulnerabilities in computer software or systems to invade the company's servers, place trojans, control the company's equipment, and complete the theft
This type of network attack technique is very common and lacks specificity. Vulnerabilities are widely present in computer software and systems, and discovering and fixing vulnerabilities is a dynamic management process that makes it difficult to completely avoid their occurrence
The National Defense University, which is directly affiliated with the US military system, has a saying: A high school student cannot spend a few nights crouching in front of a keyboard to create an F-22 fighter jet, but it is enough to create a cyber attack weapon that can destroy large enterprises and military networks
The person who first said this sentence had served in the US military and was responsible for network operations
This statement not only proves that cyber attacks are easy to launch, but also reflects the intention of the US military to develop cyber attack capabilities
This change can be seen from the changes in the US military budget
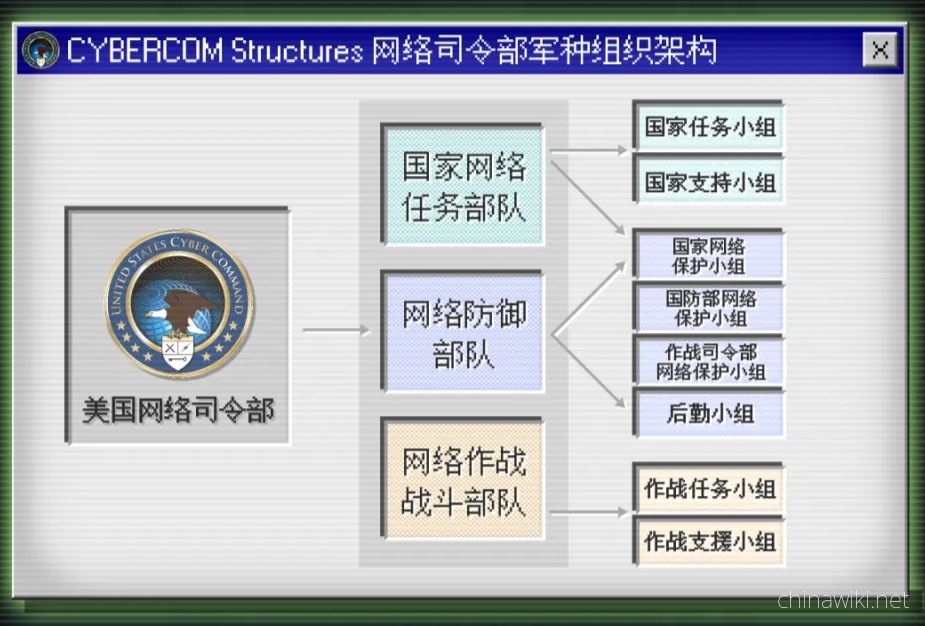
From the above figure, it can be seen that the US Cyber Command has different branches of cyber command. Originally, these military branches were each responsible for providing funding to their own cyber warfare units. In 2022, the US Congress granted the US Cyber Command greater budgetary authority to directly control the planning, projects, budgeting, and execution of US cyber warfare forces
This means that the US military's cyber warfare capabilities are beginning to integrate
In 2022, a report from the US Government Accountability Office found various problems with the method of forming cyber forces by each military branch. Another survey of frontline officers from multiple military branches found that there is a phenomenon of uneven skill training among the network forces of different military branches, and their collaborative combat capabilities are also deteriorating
It is precisely in the face of these issues that the call for establishing an independent cyber force is growing
Independent forces mean the ability to operate independently, but the US cyber forces have inherent flaws
From the job distribution of the US Cyber Command, it can be seen that only one part is truly responsible for operations, and there are two other parts: the Cyber Defense Force and the National Cyber Mission Force. As the name suggests, they are mainly responsible for defense and information technology support work
Statistics show that less than 3% of the US Cyber Command actually carries out cyber operations
That is to say, the US cyber forces originally focused more on defense capabilities
Therefore, in the past two years, building offensive forces has become a key direction of the US Cyber Command
This year, the US Cyber Command allocated nearly $90 million to build an offensive cyber platform. At the same time, in this year's US defense budget, multiple projects for building cyber weapons explicitly mention the need to incorporate offensive networks into actual combat operations, create lethal cyber warfare tools, and achieve comprehensive cyber offensive operations
In this context, it is timely and necessary for us to announce the US cyber attack on our large technology enterprise institutions. Because while building its cyber warfare capabilities, the United States is also attempting to shape international rules in cyberspace
Currently, there are two sets of international rules regarding cyberspace: the United States advocates that cyber attacks should be classified as legal and illegal, cyber attacks for national security, military, intelligence, and other reasons are legal, and only commercial espionage is illegal. So the United States has always disguised its attacks as legitimate and accused other countries of commercial espionage. Countries represented by China advocate the theory of cyber sovereignty, stating that any form of cyber attack is illegal
The reason why the United States has such a binary division is to facilitate its own fabrication of "security" reasons to launch cyber attacks on other countries at any time, because the United States adopts a "presumption of guilt" approach - after sorting out the process of launching cyber attacks by the United States, Tan Zhu found that as long as it believes that the other party "may" pose a security threat to the United States, it will unilaterally launch cyber attacks
This time, the United States launched cyber attacks on Chinese companies for its own competitive interests, stealing trade secrets, which clearly does not even comply with the United States' own "legitimate" reasons. This also thoroughly exposes the hypocrisy of the United States' binary division of cyber attacks
This once again demonstrates that the United States' malicious intentions to suppress China have not changed. If there is no competition, then steal and rob. This is the essence of bandits
The United States has started using this method to steal trade secrets from Chinese companies
-
Pay homage to Chinese astronauts: comparison of Nie Haisheng's three expeditions to space
Views: 11 Time 2021-06-18 -
Several heroic units of the people's air force are equipped with j-20 fighters
The air force announced today (18th) that the jian-20, a new generation of stealth fighter Made in China, is equipped with a number of heroic units of the people's air force.
Views: 15 Time 2021-06-18 -
Late at night, Dezhou post-90s police fainted in the duty room
at 23:18 on June 16, Wang Chen, a policeman from the central police station of Leling Public Security Bureau of Dezhou City,
Views: 21 Time 2021-06-21 -
China Academy of Criminal Police competes to sell 54 out of training dogs: Han De Mu, etc., which are required not to be abandoned
Announcement on the sale of obsolete dogs. Screenshot China Criminal Police Academy recently announced that it will sell several dogs, including German shepherd, horse dog and other breeds, which will be tested and eliminated. It requires buyers not to ab
Views: 17 Time 2021-06-24 -
Doctors warn against blind superstition that Pian Zi Huang is not a health care drug
Recently, due to the fact that Pianzihuang, a traditional Chinese medicine, has been stir fried from 590 yuan / tablet to more than 1000 yuan, which has aroused heated discussion. In many places, Pianzihuang is limited to purchase or even out of stock. Ho
Views: 15 Time 2021-06-26 -
A visit to the family of Guo Xinzhen, the archetype of the lost orphan: his adoptive parents and two elder sisters buy a new house and car for him
Guo Xinzhen once said in an interview that his adoptive parents are relatively old and they have nurtured him and need to be taken care of. His work is still in Henan, so he still wants to stay in Henan in the future, but he has many holidays and will oft
Views: 33 Time 2021-07-14 -
It is said that Wang Feng and Zhang Ziyi divorced, and Zhang Ziyi responded: false
On the evening of December 22, the media asked Zhang Ziyi's staff for confirmation of singer Huang an's disclosure of Zhang Ziyi's divorce from Wang Feng. The other party said it was a rumor.
Views: 33 Time 2021-12-23 -
Jack Ma appears in Alibaba's new global headquarters park
On November 29th, according to a reporter from The Paper, Alibaba founder Jack Ma appeared in the Alibaba Xixi C area located in Hangzhou Future Science and Technology City. This is the area that Alibaba officially put into use in May this year and is als
Views: 36 Time 2024-11-29 -
The new visa free policy benefits China in all aspects
With more and more tourists from countries receiving visa free entry to China, China's tourism and business industries have become winners, and exchanges and mutual understanding between China and foreign countries have also been strengthened.
Views: 16 Time 2024-12-09 -
China's foreign trade continues to maintain growth momentum
According to data released by the General Administration of Customs of China on the 10th, China's exports denominated in US dollars in November increased by 6.7% year-on-year
Views: 48 Time 2024-12-10 -
China independently developed double shield tunnel hard rock excavation machine and put it into use
On January 5, 2025, the first double shield hard rock excavation machine "Jianghan Ping'an" jointly developed by China South to North Water Diversion Group Jianghan Water Network Construction and Development Co., Ltd., China Railway Equipment an
Views: 22 Time 2025-01-05 -
Education cannot abandon the most fundamental aspects
Inside the venue, member Xu Kun from Beijing University of Posts and Telecommunications brought practical reflections: "Artificial intelligence has...
Views: 31 Time 2025-03-08





